How to Use Nmap Port Scan with Commands?

Introduction
In the realm of network security and exploration, understanding ports and conducting port scans is essential. Ports are endpoints that enable communication between different devices over a network. To ensure the security and accessibility of a network, it is crucial to identify open ports and potential vulnerabilities. One powerful tool for conducting port scans is Nmap (Network Mapper), a versatile and widely used open-source network scanning utility.
With this blog post, we will delve into the world of Nmap port scan and explore how to use it for port scanning. We will cover the basics of ports, walk you through the process of conducting port scans with the Nmap port scan command, and introduce you to some essential Nmap commands. By the end of this article, you will have a solid understanding of how to utilize Nmap to identify open ports and evaluate the security of your network.
What Are Nmap Ports?
In computer networking, ports serve as virtual endpoints that enable communication between devices over a network. They play a crucial role in the transmission of data, ensuring that the right information reaches the correct destination.
Each port is identified by a unique number, known as the port number, which helps in distinguishing between various types of network traffic. The Internet Assigned Numbers Authority (IANA) has standardized and assigned specific port numbers to commonly used protocols and services. These standardized port numbers make it easier for devices and applications to communicate with each other effectively.
Let’s take a closer look at the two main types of ports:
Transmission Control Protocol (TCP) Ports:
TCP ports are connection-oriented and provide reliable and ordered communication between devices. When data is transmitted over TCP, it is broken down into smaller chunks called packets. Each packet contains information about the source and destination ports, ensuring that the data arrives in the correct order and without any loss or corruption.
User Datagram Protocol (UDP) Ports:
UDP ports, in contrast to TCP, are connectionless and provide faster but less reliable communication. When data is sent over UDP, it is divided into packets, similar to TCP. However, UDP does not establish a dedicated connection or perform error checking to ensure the delivery of packets.
It’s important to note that ports range from 0 to 65535, with certain port numbers reserved for specific purposes. The well-known ports, numbered from 0 to 1023, are commonly used by standard protocols and services. Registered ports that range from 1024 to 49151 are assigned by IANA for particular applications or services. Dynamic ports, from 49152 to 65535, are available for use by applications dynamically as needed.
By analyzing the open ports on a device, one can gain insights into the available services and potentially detect any unauthorized access or exposed services.
How to Scan Nmap Ports?
Nmap is a powerful command-line tool that can perform various network scanning tasks, including port scanning. It is available for multiple operating systems and provides a wide range of options and flexibility. Here’s a step-by-step guide on how to perform port scans with Nmap:
Step 1: Install Nmap: Start by installing Nmap on your operating system. You can download Nmap from the official website (https://nmap.org/) or use the package manager specific to your operating system.
Step 2: Identify the Target: Determine the IP address of the target system you wish to scan for open ports. For example, let’s say the target system’s IP address is 192.168.0.100.
Step 3: Perform a Basic Port Scan: To conduct a basic port scan, open a terminal or command prompt and run the following command:
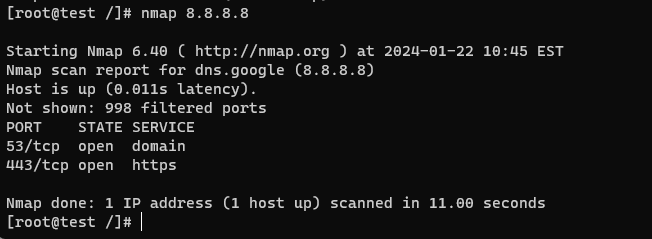
nmap 192.168.0.100Replace “192.168.0.100” with the actual IP address of your target system. This command will initiate a scan on the target system and display a list of open ports and the services associated with them.
Also Read: Learn to use SCP Command in Linux (with Examples)
Nmap scan all ports command
TCP Connect Scan (-sT)
The TCP Connect Scan is the default scan type used by Nmap ports. It establishes a full TCP connection with the target system by completing the three-way handshake. It sends SYN packets to the target ports and waits for SYN-ACK responses to determine if the ports are open, closed, or filtered.
Note : Nmap is indicating that it couldn’t establish if the host is up or not. Adding the -Pn option disables host discovery, and it might allow you to perform a TCP scan
Command: nmap -sT <target>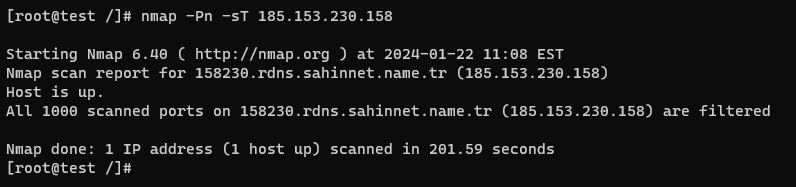
SYN Stealth Scan (-sS)
Also known as a half-open scan, the SYN Stealth Scan is one of the most popular and commonly used scan types. It transmits SYN packets to the ports that are targeted, but instead of completing the full TCP connection, it analyzes the response packets to decide if the ports are open, closed, or filtered. This scan is often faster and more stealthy than the TCP Connect Scan.
Command: nmap -sS <target>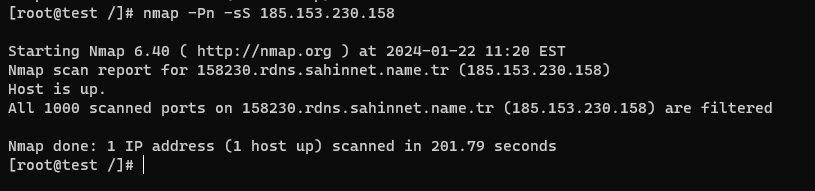
UDP Scan (-sU)
While TCP is the most prevalent employed protocol, some services and applications rely on the UDP protocol. The UDP Scan allows Nmap to send UDP packets to specific ports and analyze the responses to identify open, closed, or filtered ports. This scan can be useful for discovering services that may be running on UDP ports.
Command: nmap -sU <target>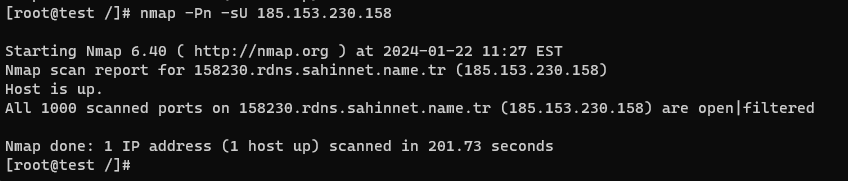
Comprehensive Scan (-sC)
The Comprehensive Scan, also known as the Script Scan, combines multiple Nmap scripts to gather detailed information about the target system. It performs a variety of tests, including version detection, vulnerability assessment, and enumeration of services and protocols.
Command: nmap -sC <target>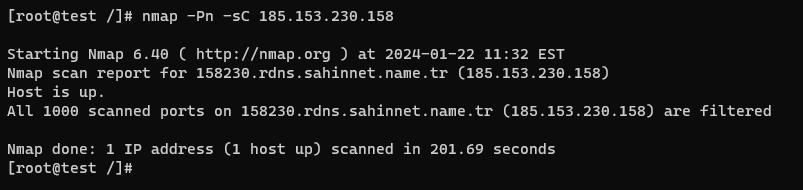
Operating System Detection (-O)
Nmap can attempt to identify the operating system of the target system by analyzing various network characteristics and comparing them against its database. This can provide valuable information about the target’s underlying infrastructure.
Command: nmap -O <target>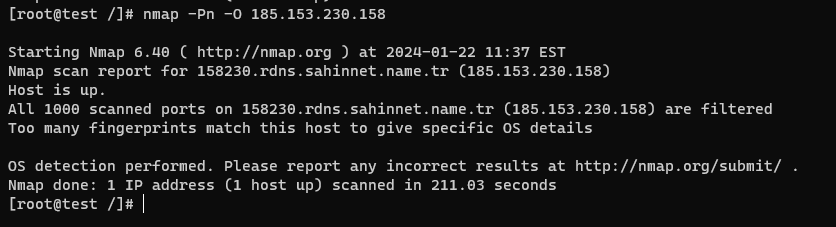
Ping Scan (-sn)
The Ping Scan, also known as the Host Discovery Scan, is used to identify active hosts on a network without scanning any ports. It sends ICMP Echo Request packets (ping) to the target systems and listens for the ICMP Echo Reply packets to determine if the hosts are up.
Command: nmap -sn <target>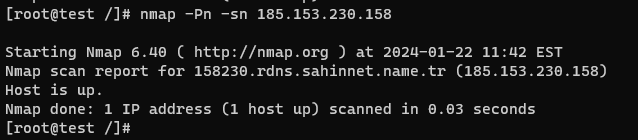
Each scan type offers different capabilities and advantages depending on the goals of your network reconnaissance. It’s critical to choose the appropriate scan type based on your specific requirements and objectives.
Also Read: DNS Cache Flushing: Troubleshooting Guide for All Operating Systems
Conclusion
In this blog post, we explored the process of using Nmap port scan. We began by understanding the basics of ports and their significance in network communication. We then learned how to perform nmap port scan commands, starting with a basic scan and progressing to a comprehensive scan that covers all ports. Nmap’s flexibility and extensive feature set make it an invaluable tool for network administrators and security professionals. Remember, port scanning should always be performed ethically and with proper authorization.